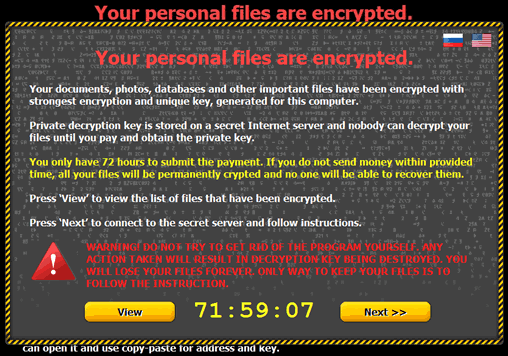
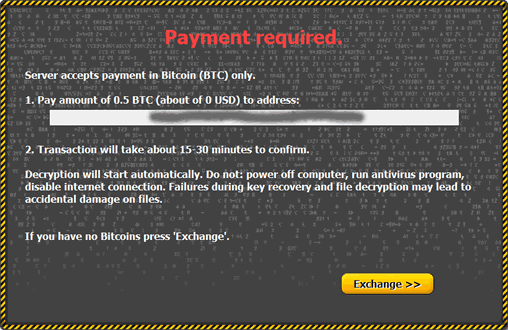
| CryptoWall | CryptoLocker |
| GAV: Crypwall.H (Trojan) GAV: Cryptodef.GF (Trojan) GAV: Cryptodef.MD (Trojan) GAV: Cryptodef.GK (Trojan) GAV: Filecoder.V (Trojan) GAV: Filecoder.CQ_3 (Trojan) GAV: Filecoder.W_20 (Trojan) GAV: Crypwall.H (Trojan) GAV: Cryptodef.GF (Trojan) GAV: Cryptodef.MD (Trojan) GAV: Cryptodef.GK (Trojan) GAV: Filecoder.V (Trojan) GAV: Filecoder.CQ_3 (Trojan) GAV: Filecoder.W_20 (Trojan) GAV: Crypwall.H (Trojan) GAV: Cryptodef.GF (Trojan) GAV: Cryptodef.MD (Trojan) GAV: Cryptodef.GK (Trojan) GAV: Filecoder.V (Trojan) GAV: Filecoder.CQ_3 (Trojan) GAV: Filecoder.W_20 (Trojan)CryptoWall 2.0 GAV: Cryptowall.A (Trojan) IPS: Adobe Flash Player Integer Overflow 2 – SID 5671 |
GAV: Filecoder.BQ (Trojan) GAV: Filecoder.BQ_6 – 8 (Trojan) GAV: Filecoder.BQ_12 (Trojan) GAV: Filecoder.BQ_17 (Trojan) GAV: Filecoder.BH_7 – 8 (Trojan) GAV: Filecoder.BH_11 (Trojan) GAV: Filecoder.W (Trojan) GAV: Filecoder.NAC (Trojan) GAV: Filecoder.NAC_4 (Trojan) GAV: FileCoder.A_2 – 5 (Trojan) GAV: FileCoder.A_11 – 12 (Trojan) GAV: FileCoder.A_16 (Trojan) GAV: FileCoder.A_24 (Trojan)IPS: Cryptolocker Infection Activity 1 – SID 7559 IPS: Cryptolocker Infection Activity 2 – SID 9728 IPS: Cryptolocker Infection Activity 3 – SID 9737 |
Para mais informações sobre novos malwares, siga os link abaixo:
https://mysonicwall.com/sonicalert/sonicalert.aspx
Proteção contra malware no Dell SonicWALL
Em um Next Generation Firewall Dell SonicWALL, siga os passos abaixo para estar protegido contra malwares:
1. Gateway Anti-virus (GAV)
- Make sure GAV is updated with the latest signatures.
- Enable GAV.
- Enable Cloud GAV
- Enable Inbound and Outbound inspection of HTTP, FTP, IMAP, SMTP, POP3, CIFS/Netbios and TCP Stream.
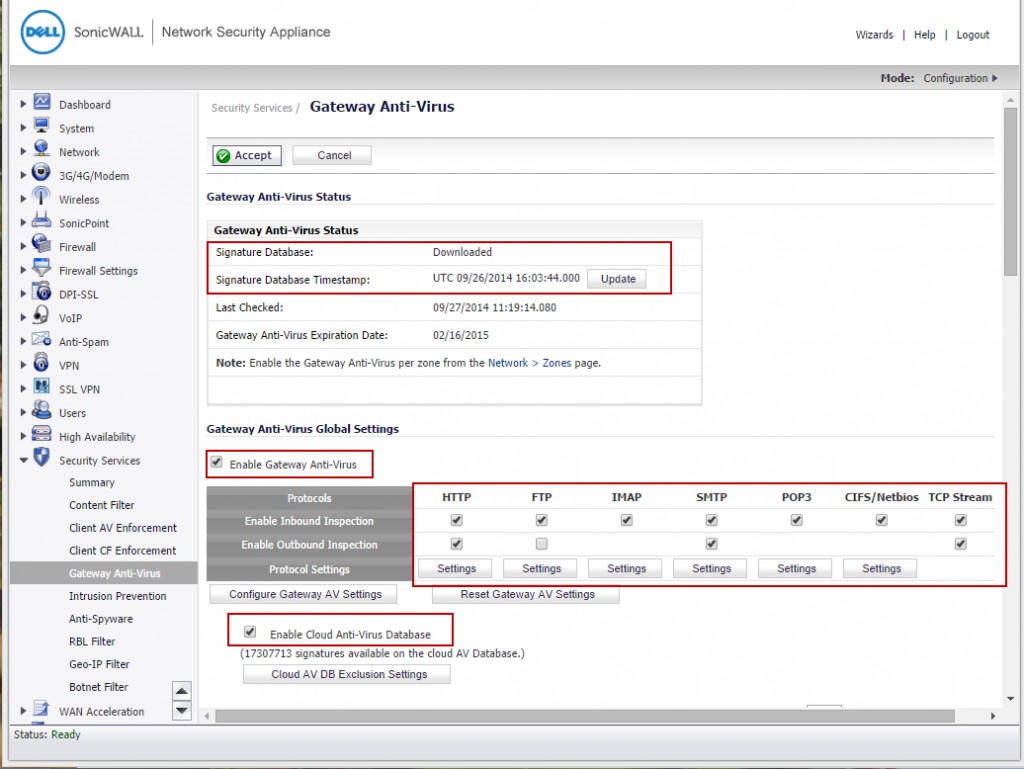
- Under the settings of each protocol (HTTP etc), enable the check boxes under
- Restrict Transfer of password-protected ZIP files
- Restrict Transfer of MS-Office type files containing macros (VBA 5 and above)
- Restrict Transfer of packed executable files (UPX, FSG, etc.)
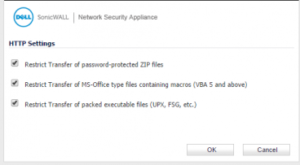 Click To See Full Image.
Click To See Full Image.
- Enable GAV on all internal and external zones under Network > Zones.
2. Intrusion Prevention Service (IPS)
- Make sure IPS is updated with the latest signatures.
- Enable prevention of Medium and High Priority Attacks. This will automatically include the signatures for this malware
- Enable IPS on all internal and external zones under Network > Zones.
3. Botnet Filter
Enabling Botnet Filter will block access to known command and control servers of this malware.
- On the Security Services > Botnet Filter page, enable the check box, Block connections to/from Botnet Command and Control Servers
- Enable the check box Enable Logging
4. Content Filter Service (CFS)
Enable CFS and configure to block sites in the “Malware” and “Hacking/Proxy Avoidance Systems”
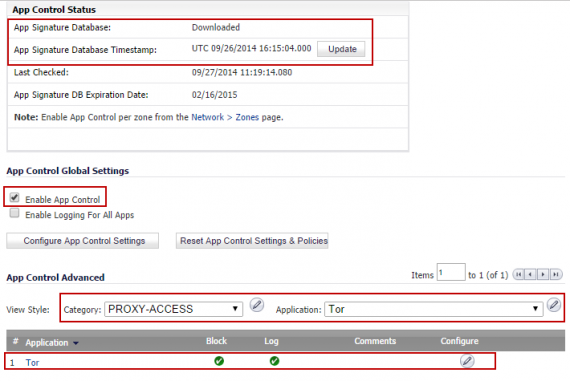
5. App Control Advanced
CryptoWall is known to use TOR to obtain the encryption keys used for encrypting files. Therefore, use App Control Advanced to block TOR. By enabling the signatures for TOR, CryptoWall will not be able to obtain the keys needed to encrypt files thus mitigating further damage to the infected host computer.
- On the Firewall > App Control Advanced page, select Category as PROXY-ACCESS
- Set Application to TOR.
- Click on Configure under Application with TOR selected.
- Set Block and Log to Enable.
- Click on OK to save.
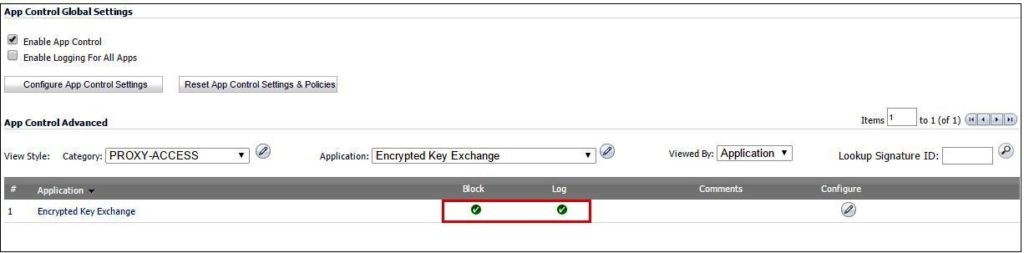
Tor will use Encrypted key exchange application,inorder to block that,
- On the Firewall > App Control Advanced page, select Category as PROXY-ACCESS
- Set Application to encrypted key exchange
- Click on Configure under Application with Encrypted key exchange selected.
- Set Block and Log to Enable.
- Click on OK to save.
 6. DPI-SSL Client Inspection
6. DPI-SSL Client Inspection
Enabling Client DPI-SSL, although not a mandatory measure, would provide additional security because 1) almost all web and email traffic is over SSL. For example, if a spam email is received over SSL, SonicWALL will not be able to detect the malware contents, if any, in it. 2) initial connection to TOR gateway is over SSL. Enabling DPI-SSL will allow SonicWALL to decrypt such traffic and scan it for malware. Under the DPI-SSL > Enable SSL Client Inspection page, enable the check boxes under Gateway Anti-virus and Intrusion Prevention.
7. CryptoWall or CryptoLocker infection may not always happen over the Internet. It could occur over shared files and/or drives or over shared removable media like USB thumb drives and external hard disks. Therefore, Administrators are advised to adhere to basic system level security best practices to protect internal hosts in the network from being infected.